
Security pack










Discover 24/7 solutions for your website. Empower control, observation, and unmatched protection.
Explore the cutting-edge world of security enhancements, enriched by our innovative features. Discover a new level of protection that combines advanced technology with intuitive solutions.
Open source community
Be part of the story

Be part of the story

Security pack

Right on time

Coffee time

Navigate and manage the complex world of cyber security effortlessly.
Keep your online assets under vigilant surveillance.

Seamlessly integrate with various platforms.
Get instant notification for anomalies for your digital assets.
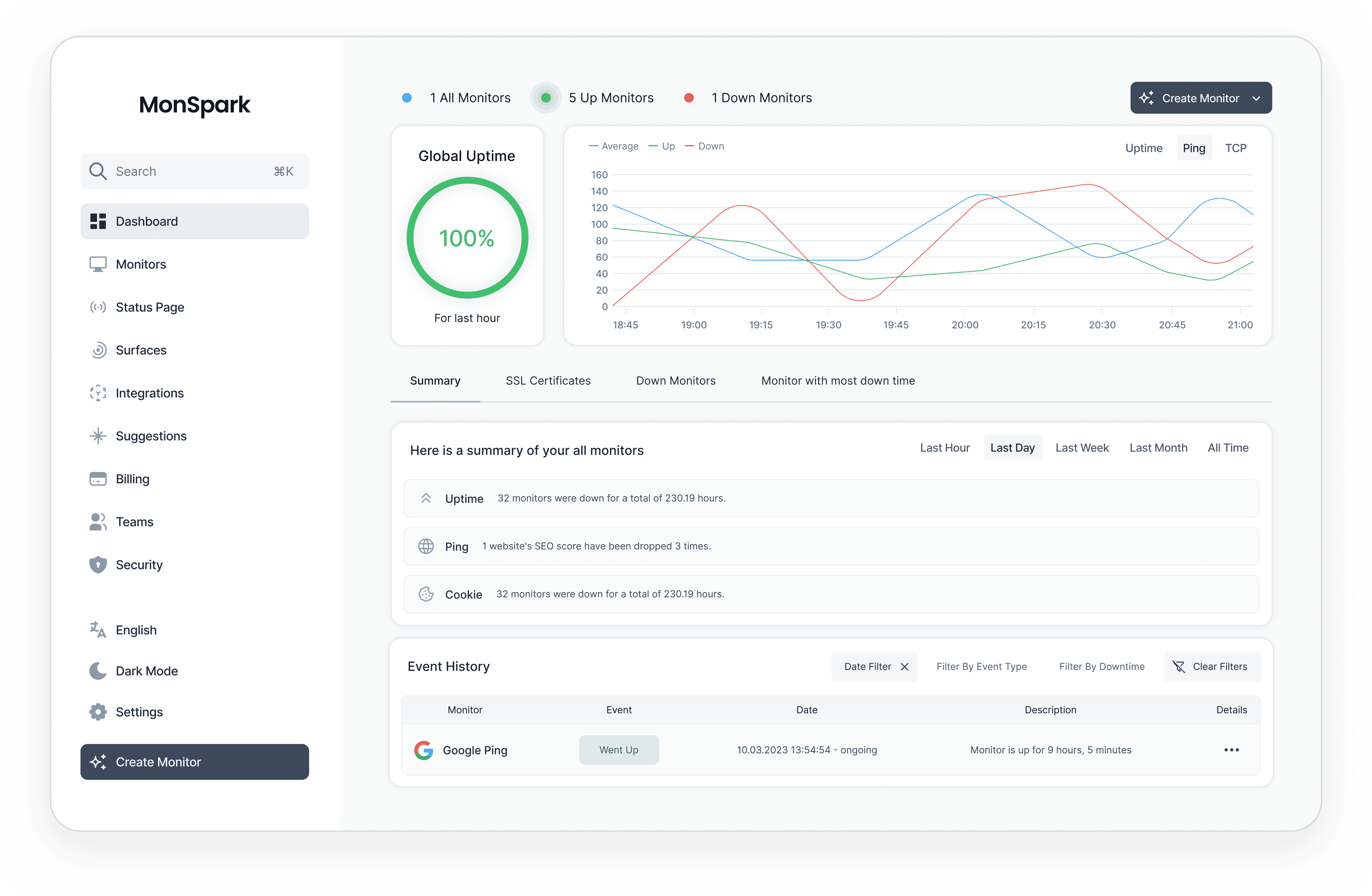
Monitor your websites and servers 24/7 with MonSpark and be the first one when something goes wrong.

MonSpark ensures uninterrupted monitoring for your websites.
Receive instant notifications when your website goes down.
You can customize monitoring frequency and notification preferences.
A guide where you can find quick and informative answers to your queries about Peyk.

Peyk offers comprehensive web application and server monitoring solutions through its MonSpark platform. With a presence in over 130 countries, Peyk ensures uninterrupted and efficient operation by monitoring web applications and servers 24/7. Its innovative technology provides real-time alerts via various channels, including Teams, email, SMS, and phone calls, enabling swift action in the event of anomalies for seamless business continuity.
MonSpark is a comprehensive monitoring solution used in over 130 countries, encompassing both web application and server monitoring. It ensures the continuous tracking of web application performance and server metrics, promptly alerting users to issues via email, SMS, or voice calls. The platform monitors diverse aspects such as uptime, functionality, resource usage, and security, enabling businesses to proactively address problems and maintain seamless digital operations.
Effortlessly begin monitoring your preferred website by creating an account on MonSpark with just a few simple clicks. Streamlined setup and user-friendly controls make it quick and easy to keep track of your website's performance in real-time.
Thanks to our highly available monitoring infrastructure, we identify anomalies on your website and alert you in few seconds through your preferred channel such as Slack, Microsoft Teams, SMS or even a phone call. write this better.
MonSpark offers integrations with SMS, phone call, Microsoft Teams, Slack, Discord, and Zapier.
We offer Cloud and on-premise licensing models.
Customer feedback is valuable to us. The input we receive from you contributes to the continuous improvement of Peyk.